For organizations using Pullfrog in private repos, all repository activity is private and all actions are triggered by trusted team members. The risks in this scenario are minimal. The rest of this document primarily applies to users who are using Pullfrog on public repos.
| Layer | Protection |
|---|---|
| System prompt | Instructs agents to refuse exfiltration attempts |
| Secret masking | Redacts secrets from all logs |
| Secret isolation | Repo secrets not passed to actions by default |
| Environment whitelisting | Only minimal env vars reach the agent subprocess |
| Short-lived tokens | GitHub tokens expire and are revoked after each run |
| Permission checks | Only collaborators can trigger runs by default |
| Protected branches | Agents cannot push directly to main/master/production |
System prompt
All runs triggered by Pullfrog include a system prompt with instructions to identify and avoid common exfiltration vectors. The boundaries of the user prompt are indicated in the structure of the prompt, so the agent knows where the system prompt ends and the user prompt begins.Secret masking
All secrets are auto-masked using GitHub’s first-party secret masking feature, so they cannot be publicly logged in GitHub Actions logs by accident.Secret isolation
Repository secrets are not automatically available to the Pullfrog action. You must explicitly pass the necessary secrets (like API keys) via environment variables in your workflow configuration. This gives you full control over which secrets are exposed to the agent.Shell environment scrubbing
Pullfrog supports a Restricted shell permission, which automatically scrubs sensitive environment variables from the Shell tool. This works across all agents.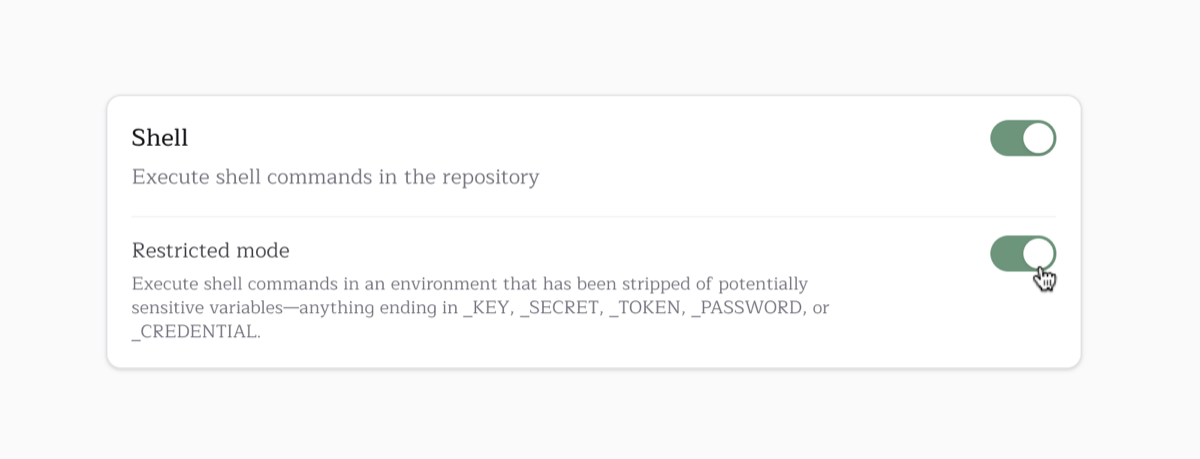
env or printenv. The shell environment is filtered to remove any variable ending in these suffixes:
-_KEY
-_SECRET
-_TOKEN
-_PASSWORD
-_CREDENTIAL
This filtering does not apply to GITHUB_TOKEN. Subprocesses always inherit the built-in GITHUB_TOKEN from GitHub Actions (which can be customized in your pullfrog.yml workflow). This ensures that standard git operations work correctly even in Restricted mode. In non-restricted mode (private repos), the Pullfrog installation token is used instead.
Note that the agent process itself receives the full environment to ensure all configured tools and integrations work correctly. The scrubbing happens at the shell execution layer, which is the primary vector for exfiltration attacks.
Restricted mode is ALWAYS ON for public repositories and cannot be disabled. Private repositories default to Enabled (full access), but can be configured to use Restricted mode if desired.
Short-lived tokens
Pullfrog uses GitHub OIDC to acquire installation tokens that are scoped to the repository and short-lived. Moreover, they are explicitly revoked at the end of each run.Permission checks
Pullfrog provides the ability to trigger agent runs in response to actions performed by non-collaborators, like mentions, new issues, and new PRs.- By default, these triggers are all disabled. This means agent runs cannot be triggered by non-collaborators unless explicitly enabled.
- Any agent runs triggered by external actions are automatically run with limited permissions. This cannot be disabled.
Protected branches
Agents cannot push directly tomain, master, or production. They must create feature branches and open pull requests.
